PE File Browser
Ever wondered which DLLs your EXE depends on? Or what technology a given DLL is built with? Is it a native DLL, a .Net DLL, or a .Net Core DLL? If it is .Net technology, which framework does it rely upon?
PE File Browser is a PE explorer that allows you to view the contents of portable executable files. All processor architectures are supported, allowing you to examine ARM executables as well as x86 and x64.
The PE File structure is well documented, with a PE file consisting of a header, an optional header and a list of directories that points to specific sections of the PE file. Normally PE files are .exe and .dll, but they can also be .bpl, .arx, .ocx, .scr, .mui, .sys, .drv.
All the information in a PE file is displayed in chunks of related data. Most of these displays relate to specific parts of a PE file. Some of these displays are synthesised to provide you with additional data that is not so readily available from the PE file (for example, the Additional Information, .Net Information and debugging symbols panels).
No more digging around trying to determine if a DLL is built with .Net, and, if so, which version of the CLR is required. That information is displayed in the .Net Information section.
Does the EXE depend on XYZ.DLL? Look at the All Dependent Modules section to find out.
Which functions from the Windows API does the DLL use? Look at the Imported Modules and Functions section to find out.
Are functions exported from this DLL actually implemented in another DLL? Look at the Exported Functions section, examining the Forwarded Functions column.
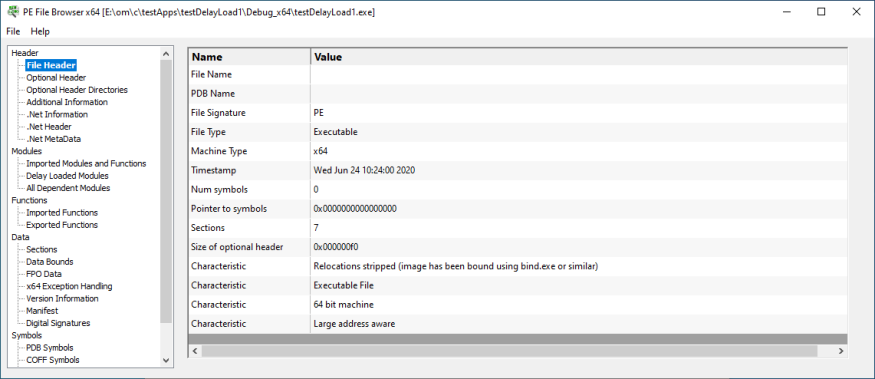
File Header
This section displays PE file header information.
- File name
- PDB name
- File signature
- File type
- Machine type
- Timestamp
- Number of symbols
- Pointer to symbols
- Number of sections
- Size of optional header
- Characteristics
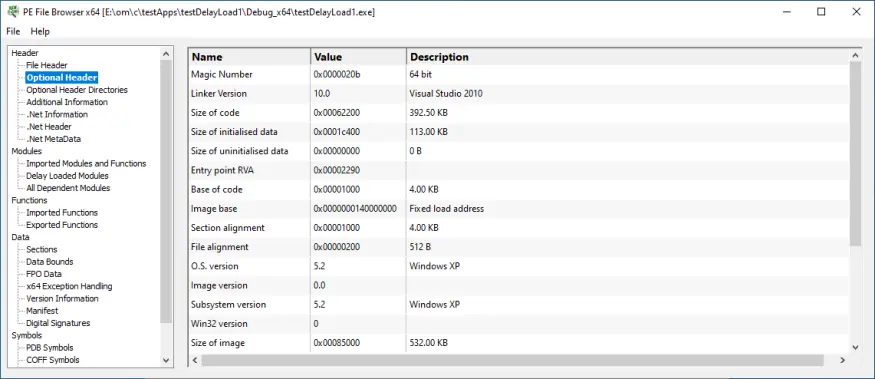
Optional Header
Information from the PE optional header.
- Section alignment
- File alignment
- OS version
- Image version
- Subsystem version
- Win32 version
- Size of image
- Size of headers
- Subsystem
- Characteristics
- Stack size reserve
- Stack size commit
- Heap size reserve
- Heap size commit
- Loader flags
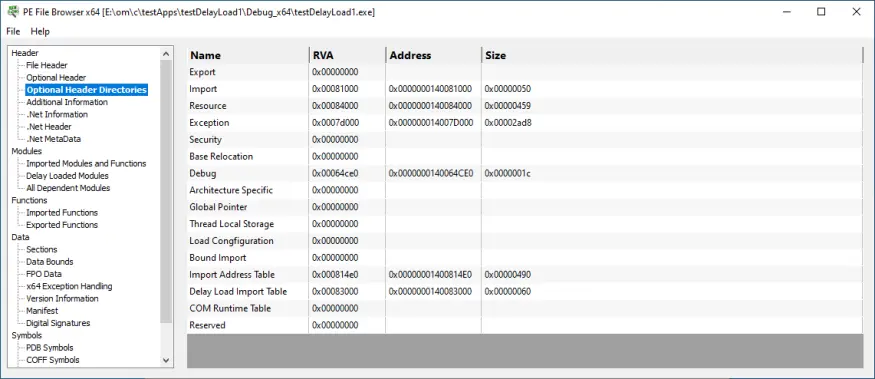
Optional Header Directories
Information from the PE optional header directories.
- Export
- Import
- Resource
- Exception
- Security / Certificate table
- Base relocation
- Debug
- Architecture specific
- Global pointer
- Thread local storage
- Load configuration
- Bound import
- Import address table
- Delay load import table
- CLR / COM runtime table
- Reserved
For each directory we display
- Name
- RVA
- Address
- Size
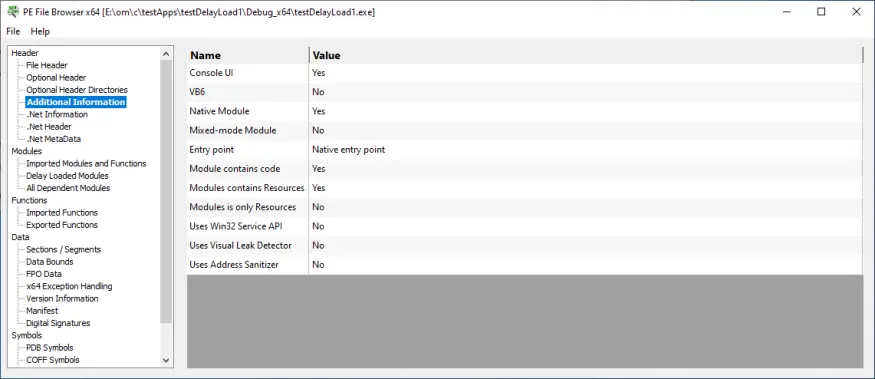
Additional Information
Information about the module entry point and the type of application.
- VB6
- Native module
- Mixed-mode module
- Entry point type
- Module contains code
- Module contains resources
- Module only contains resources
- Module is UPX compressed
- Built using Cygwin
- Built using MSYS2
- Module has Data Execution Prevention
- Module has Control Flow Guard
- Console UI
- Uses Win32 service API
- Uses Visual Leak Detector
- Uses Address Sanitizer
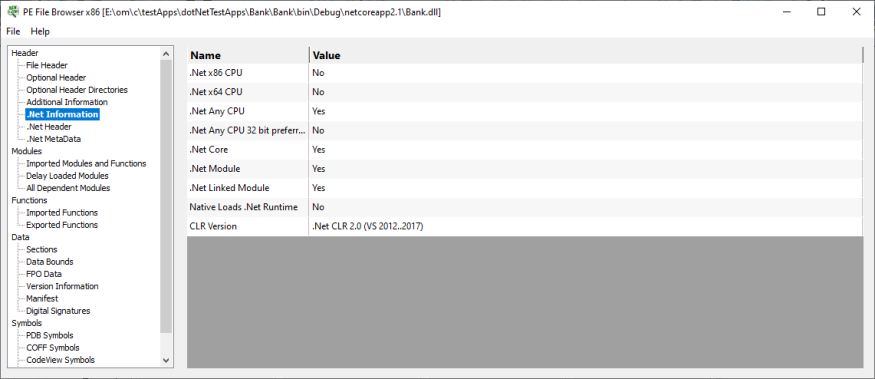
.Net Information
Information about .Net and the processors this .Net executable will run on.
- CLR Version
- .Net x86 CPU
- .Net x64 CPU
- .Net any CPU
- .Net any CPU 32 bit preferred
- .Net module
- .Net linked module
- .Net Core (Framework Dependent)
- .Net Core (Self Contained)
- Native but loads .Net runtime
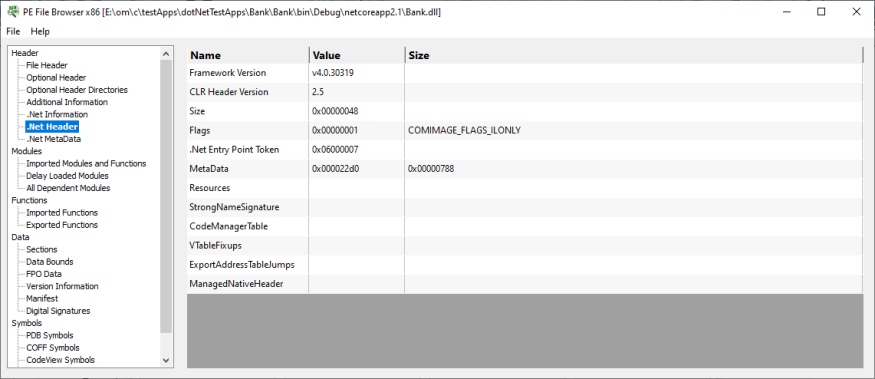
.Net Header
Information about .Net Framework and the .Net entry point.
- Framework version
- CLR header version
- Size
- Flags
- .Net entry point RVA
- Metadata
- Resources
- Strongname signature
- Code manager table
- VTable fixups
- Export address table jumps
- Managed native header
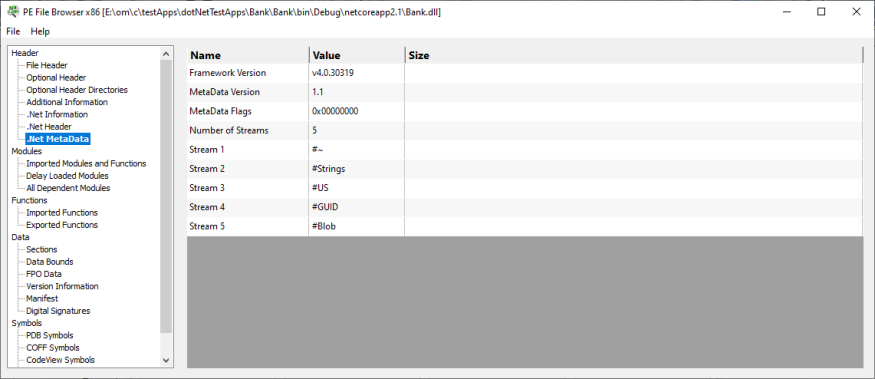
.Net MetaData
Information about .Net MetaData.
- Framework version
- Metadata version
- Metadata flags
- Number of streams
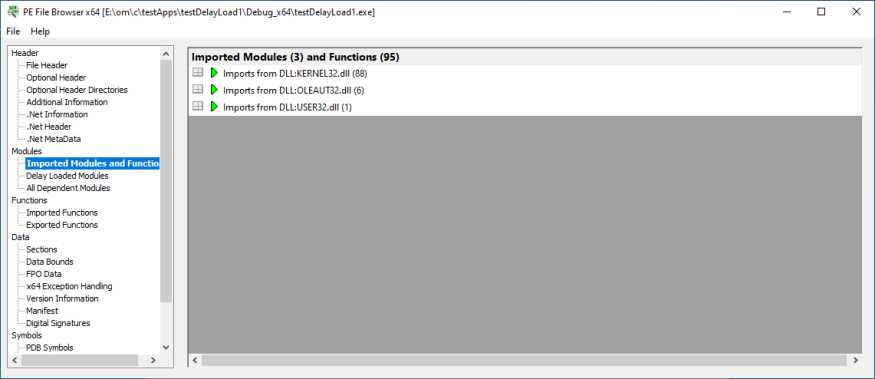
Imported Modules and Functions
The modules the DLL imports and the functions imported from those modules.
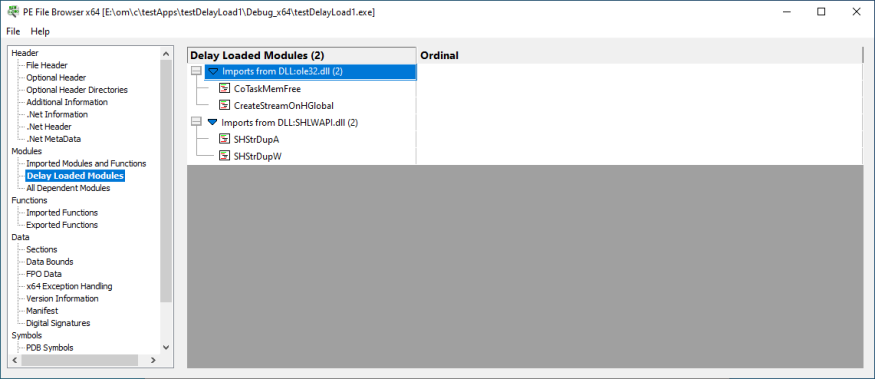
Delay Loaded Modules
The delay-loaded modules the DLL imports and the functions imported from those modules.
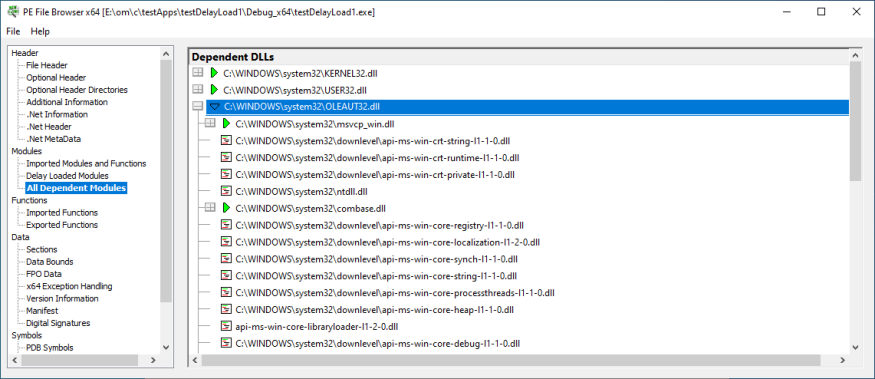
All Dependent Modules
All the modules the DLL imports. Any missing DLLs will be displayed in red.
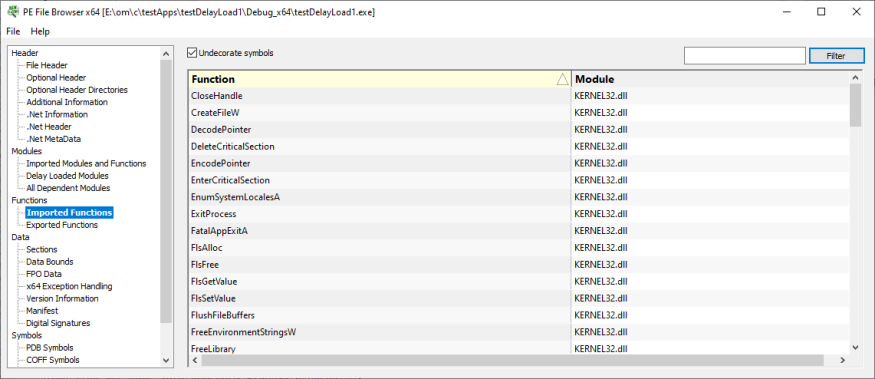
Imported Functions
The functions imported from other DLLs.
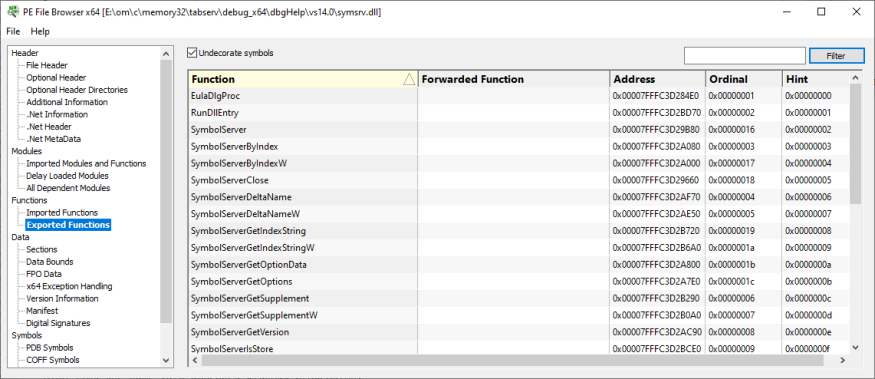
Exported Functions
The exported functions for other DLLs to use.
The Forwarded Function column indicates if a different DLL actually implements the function.
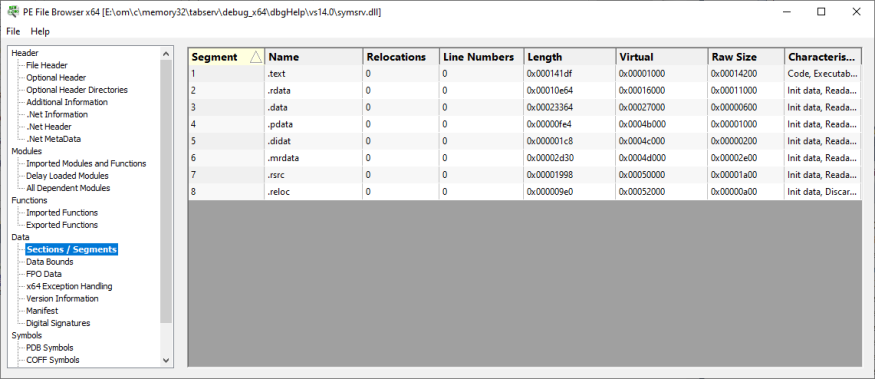
Sections / Segments
The sections that are contained within the DLL. For example: data, relocation, resource, code.
- Segment
- Name
- Relocations
- Line numbers
- Length
- Virtual
- Raw size
- Characteristics
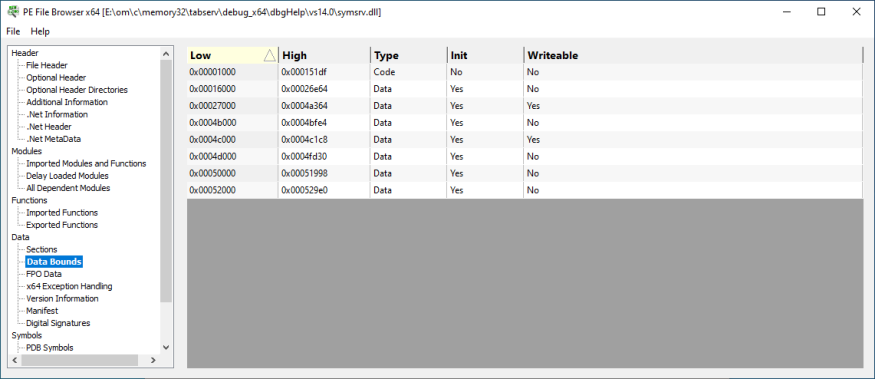
Data Bounds
The different readable, readable and writeable, and executable areas in the DLL.
- Low
- High
- Type
- Initialized
- Writeable
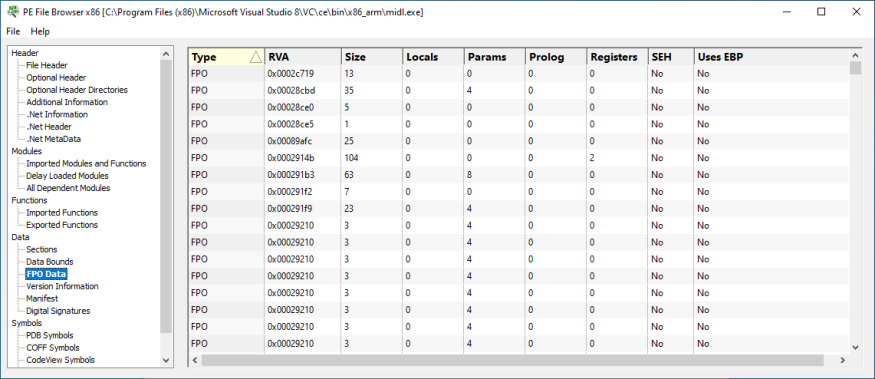
Frame Pointer Omission Data
Information about Frame Pointer Omission usage in the DLL.
- Type. (FPO, Trap, TSS, Non-FPO).
- RVA
- Size
- Locals
- Params
- Prolog
- Registers
- SEH
- Uses EBP
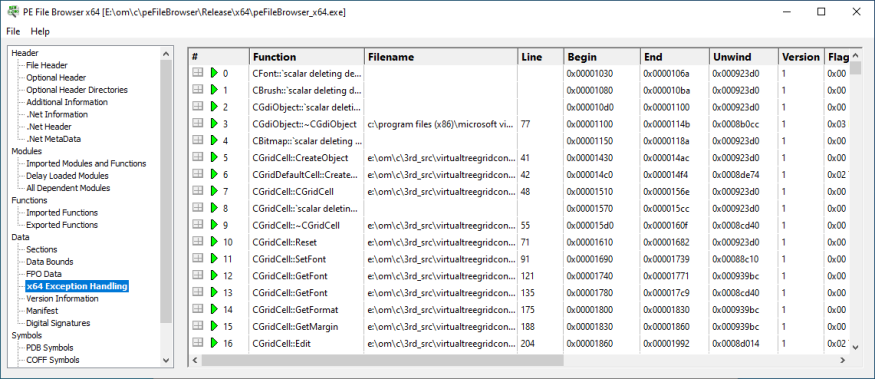
x64 Exception Handling Data
Information about the table-based exception handling mechanism used by x64 executables. The data displayed are RUNTIME_FUNCTION data.
This information panel is only displayed for 64 bit executables.
- Function
- File name
- Line number
- Begin RVA
- End RVA
- Unwind RVA
- Version
- Flags
- Prolog
- Frame register
- Frame offset
- Codes
- Exception RVA
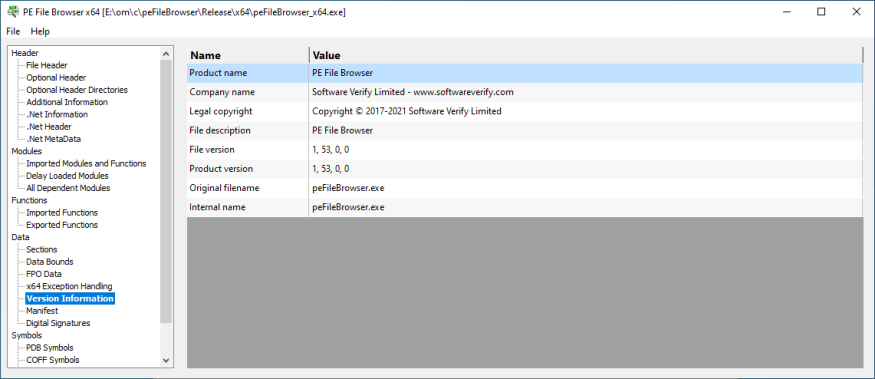
Version Information
Information from the version resource.
- Name
- Value
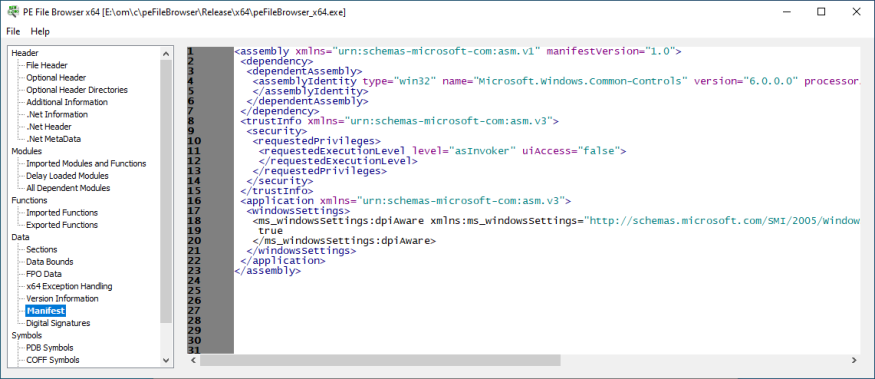
Manifest
Information from the DLL manifest.
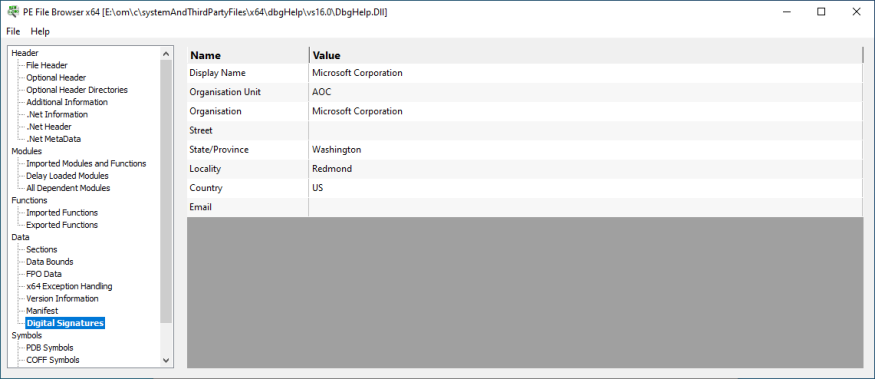
Digital Signatures
Information about the digital signatures for the DLL.
- Name
- Value
Thread Local Storage
Information about thread local storage for the DLL.
- Name
- Value
- Comment
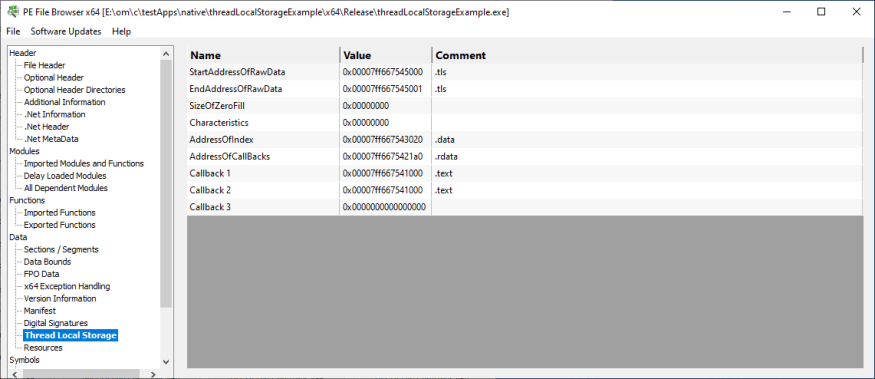
Malicious binaries often use thread local storage as a means to inject code into a target application, with a view to gaining elevated privileges on the computer system. You can check the module to see if it has any Thread Local Storage.
Thread Local Storage is not necessarily malicious, but if you find a module that you think has been tampered with and it has Thread Local Storage that may be of interest.
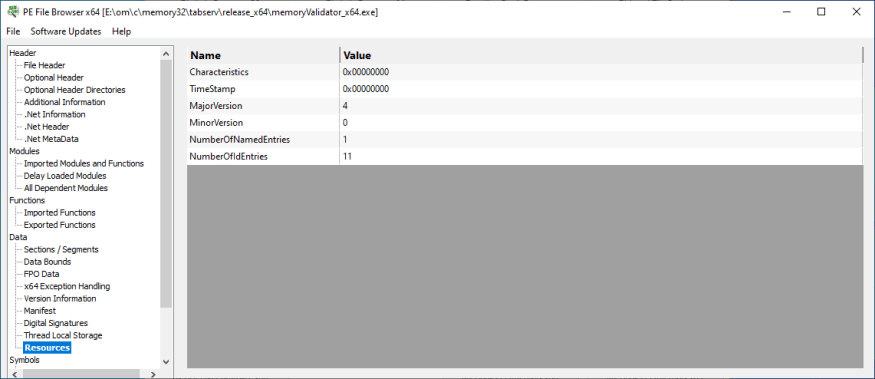
Resources
Information about resources stored in the DLL.
- Name
- Value
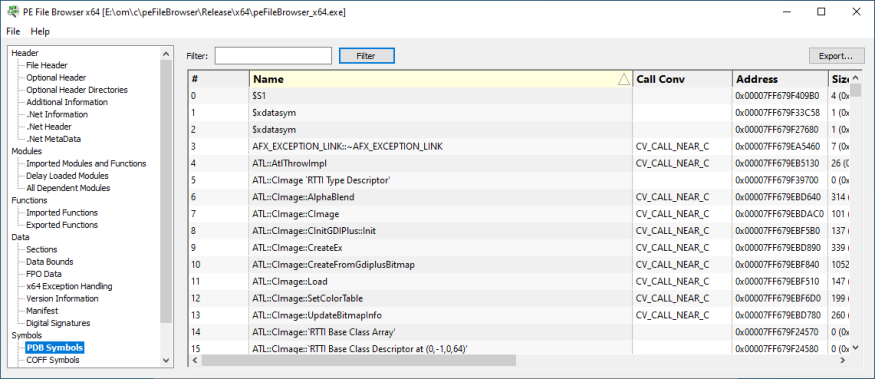
PDB Symbols
Debugging symbols from the DLL’s PDB file.
- Name
- Calling convention
- Address
- Size
- Type
- Flags
- Line number
- File name
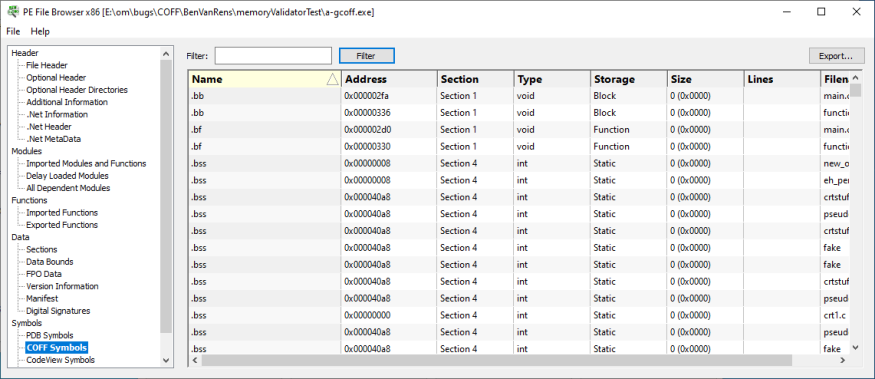
COFF Symbols
COFF Debugging symbols for the DLL.
- Name
- Address
- Section
- Type
- Storage
- Size
- Lines
- File name
CodeView Symbols
CodeView Debugging symbols for the DLL.
- Name
- Type
- Address
- Offset
- Line number
- File name
STABS Symbols
STABS Debugging symbols for the DLL.
- Name
- Address
- Section
- Type
- Storage
- Size
- File name
Misc Debug Data Symbols
Miscellaneous debug data for the DLL.
- Name