Scenario:
A customer has supplied you with a crash report containing a callstack with addresses. The callstack also indicates which module relates to which address.
The customer has also supplied you with a list of module load addresses.
Example Data:
Exception code: C0000005 ACCESS_VIOLATION
Fault address: 0x005f5eec (base 0x00400000) C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe
Exception Parameters:
0: 0x00000000 [Read Error]
1: 0x035f0034 [Address]
Registers:
EAX:035F0034
EBX:00000000
ECX:FFFDD000
EDX:00002370
ESI:006F7D58
EDI:035F0034
CS:EIP:0023:005F5EEC
SS:ESP:002B:0018FE14 EBP:0018FE3C
DS:002B ES:002B FS:0053 GS:002B
Flags:00010202
StackTrace
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x005F249C
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x005F23C3
C:\Windows\syswow64\msvcrt.dll : 0x75D70000 : 0x75D7C3E4
C:\Windows\syswow64\msvcrt.dll : 0x75D70000 : 0x75D836B6
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x0060AA42
C:\Windows\syswow64\kernel32.dll : 0x754D0000 : 0x754E3365
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F6D
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F40
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F40
This is data from a real crash a few years ago, from C++ Memory Validator 5.80.
Question:
How do you decode these absolute addresses?
Answer:
In the above data we can see a callstack containing entries for ntdll.dll, msvcrt.dll, and memoryValidator.exe.
All the modules are Microsoft DLLs except for the EXE, which is part of C++ Memory Validator, one of our tools.
To decode these values, we load memoryValidator.exe into TDSBrowser.exe, then for each symbol we take the following actions.
For our purposes here, we're going to show how to convert one symbol. We're going to use the first symbol from memoryValidator.exe in the example data above.
0x005f5eec (base 0x00400000)
The address is 0x005f5eec. The DLL loaded at 0x00400000. You'll notice the load address for all MemoryValidator.exe entries is 0x00400000.
From the Query menu choose Find Symbol with Absolute Address....

The Query Symbol by Absolute Address dialog is displayed.
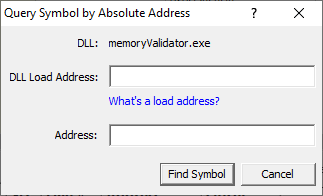
Type the DLL load address into the DLL Load Address field. Prefix any hexadecimal addresses with 0x.
Type the symbol address into the Address field. Prefix any hexadecimal addresses with 0x.
Click the Find Symbol button.
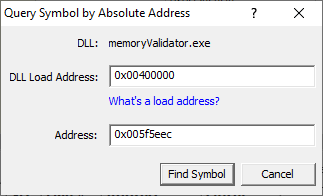
The appropriate location in the code is found and displayed.
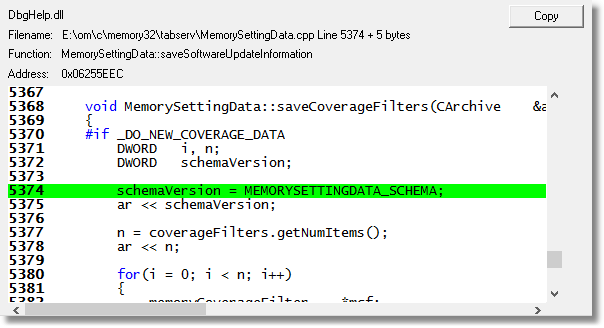
Results:
Repeating the process for the data shown above resulted in this information.
0x005f5eec (base 0x00400000) C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe MemorySettingsData::saveCoverageFilters MemorySettinData.cpp 5374
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x005F249C MemorySettingData::writeRegistrySimple MemorySettingData.cpp 3827
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x005F23C3 MemorySettingData::writeRegistrySimple MemorySettingData.cpp 3821
C:\Windows\syswow64\msvcrt.dll : 0x75D70000 : 0x75D7C3E4
C:\Windows\syswow64\msvcrt.dll : 0x75D70000 : 0x75D836B6
C:\Program Files (x86)\Software Verification\C++ Memory Validator\memoryValidator.exe : 0x00400000 : 0x0060AA42 std::_Tree<...very big template...>::erase xtree Line 351
C:\Windows\syswow64\kernel32.dll : 0x754D0000 : 0x754E3365
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F6D
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F40
C:\Windows\SysWOW64\ntdll.dll : 0x77920000 : 0x77959F40
Help! I have a crash address but I don't know what the load address is? What do I do?
You need to read about load addresses.