Scenario:
A customer has supplied you with data from Windows Event Viewer about a crash. The log contains XML and you don't know which values are relevant.
The event log data will have a provider name of "Windows Error Reporting" or "Application Error".
The XML data is found on the "Details" tab with the XML View radio box selected.
Example Data:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Windows Error Reporting" />
<EventID Qualifiers="0">1001</EventID>
<Level>4</Level>
<Task>0</Task>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2020-02-10T17:39:08.000000000Z" />
<EventRecordID>260219</EventRecordID>
<Channel>Application</Channel>
<Computer>hydra</Computer>
<Security />
</System>
<EventData>
<Data>2023787729086567941</Data>
<Data>1</Data>
<Data>APPCRASH</Data>
<Data>Not available</Data>
<Data>0</Data>
<Data>testDeliberateCrash.exe</Data>
<Data>1.0.0.1</Data>
<Data>5e419525</Data>
<Data>testDeliberateCrash.exe</Data>
<Data>1.0.0.1</Data>
<Data>5e419525</Data>
<Data>c0000005</Data>
<Data>000017b2</Data>
<Data />
<Data />
<Data>C:\Users\stephen\AppData\Local\Temp\WERA14E.tmp.WERInternalMetadata.xml</Data>
<Data>C:\Users\stephen\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_testDeliberateCr_c31b903842d94a84d4621dceaac377462674f7a_eb589596_3a75a48a</Data>
<Data />
<Data>0</Data>
<Data>3cc45263-4c2c-11ea-83d3-001e4fdb3956</Data>
<Data>0</Data>
<Data>54756af49aec84f97c15f03794ffd605</Data>
</EventData>
</Event>
This is data from a test program that is designed to crash.
Question:
There the event log indicates a DLL, but no load address, two different addresses, an exception code and an offset from the start of the DLL. How do you decode this relative offset?
Answer:
DWARF Browser has an option specifically for this occasion.
The XML data indicates the crash happened in testDeliberateCrash.exe. Load this into DWARF Browser being sure to load the correct build version so that symbols match the crash addresses.
From the Query menu choose Find Symbol from Event Viewer XML crash log....
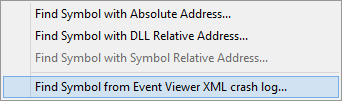
The Query Symbol by Absolute Address dialog is displayed.
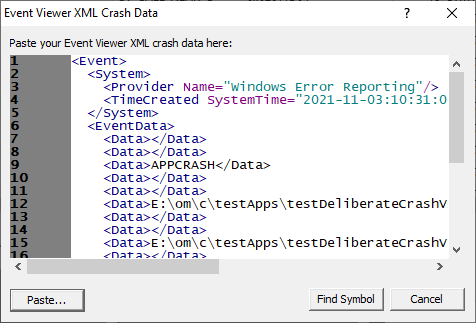
Paste the XML data from the Event Viewer into the text field.
Click the Find Symbol button.
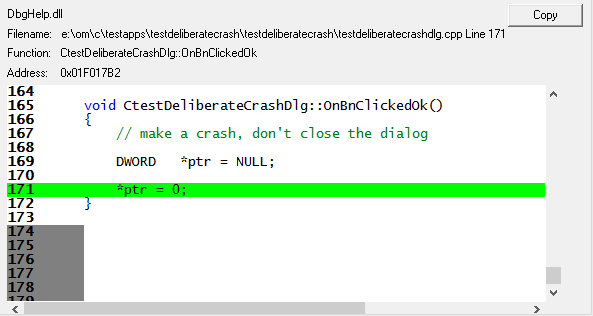
The appropriate location in the code is found and displayed.